Session is fundamentally different than most other secure messaging services.
Conversations in Session are secured using client-side E2E encryption. Only the sender and the recipient of a message can read it. But Session goes beyond providing message security. Session also protects the identities of its users. It makes your communications private and anonymous, as well as secure.
Session can do this because it connects users through a Tor-like network of thousands of Service Nodes. Service Nodes are servers that pass messages back and forth through the network as well as provide additional services. The onion request system that Session uses to protect messages ensures that no Service Node in the network ever knows both a message’s origin (your IP address) and destination (the recipient’s IP address). This allows you to hide your IP by default.
Session takes a number of additional steps to protect your identity:
- No phone number is required for registration
- No email is required for registration
- No geolocation data, device data, or metadata is collected
- Even if you are travelling in different country, there is no requirment to change sim in any country for session to work . Session will work fine whereever you go as phone number is not required in session
The Service Nodes are grouped together into swarms. Swarms provide redundancy to the network as well as temporary storage when messages cannot be delivered to their destination. Each Session client connects to a swarm to send and receive messages in real time, as well as to retrieve relevant messages that are stored in the swarm awaiting delivery.
You’ll notice that we haven’t talked about any kind of central server here. The Session network is decentralized, with no single point of failure, and no main server for bad guys to hack. Session moves messages using an onion routing system.
In an onion routing system, messages are surrounded by multiple layers of encryption and pass through multiple nodes in the system. Each node decrypts a layer of encryption before passing the message along. Because of the way the messages are encrypted, no node can know both the origin of the message and its destination. Additionally, your IP address is never visible at the destination, meaning whoever you are conversing with has no way to identify you when you use Session. The Session service should prove to be very resilient, and continue functioning even as individual Service Nodes join or leave the network.
Session’s onion routing system runs on the Oxen Service Node network. This network (formerly known as Lokinet) also serves as part of the infrastructure for the $OXEN cryptocurrency. You can learn more about OXEN at the Oxen.io website.
While Session now handles basic messaging functions very well, it doesn’t have some of the features that competitors like Signal or Telegram do. It does not yet do voice or video calls, among other things. If you need those specific capabilities, you may want to look at a different messenger app.
That’s what you need to know to understand how Session works. background information, we’re now ready to talk intelligently about Session.
Here are the pros and cons that we identified in this Session
+ Pros
- End-to-end (E2E) encryption secures text and voice messages as well as attachments
- Encryption: Session Protocol
- Does not require telephone number or email address to sign up
- Open source
- Onion routing system provides decentralization and anonymity
- Does not log IP Addresses or metadata
- Encrypted closed groups (now up to 100 people) and open groups (no limit to size)
- Successfully completed security code audit of Desktop, Android, and iOS apps
– Cons
- Does not support 2FA (two factor authentication)
- Redesigned multi-device syncing
- Perfect Forward Secrecy removed
Session feature summary
Here are features you’ll want to consider when evaluating Session:
- It uses the Signal-inspired Session Protocol, on top of a distributed onion routing system for anonymous, decentralized communication
- 100% open source code. (The code is available on GitHub.)
- Clients for Android, iOS, macOS, Windows, Linux
- The system is much more stable after several months of redesign and refactoring
Session company information
Session is a project of the Loki Foundation. The Loki Foundation (registered as LAG Foundation, LTD) is a registered charitable foundation based in Victoria, Australia. The foundation states that their purpose is to, “…build open-source, metadata-free communications tools and apps that defend privacy in the digital world.”
Where is your Session data stored?
Messages that are sent to you are actually sent to your swarm. The messages are temporarily stored on multiple Service Nodes within the swarm to provide redundancy. Once your device picks up the messages from the swarm, they are automatically deleted from the Service Nodes that were temporarily storing them.
Session clients do not act as nodes on the network, and do not relay or store messages for the network. Session’s network architecture is closer to a client-server model, where the Session application acts as the client and the Service Node swarm acts as the server. Session’s client-server architecture allows for easier asynchronous messaging (messaging when one party is offline) and onion routing-based IP address obfuscation, relative to peer-to-peer network architectures.
Launching Session highlighted one of the key differences between it and Signal: no need to enter a phone number or email address. Instead, Session gives you the opportunity to create an account by generating a Session ID, or by signing in to an existing account (by entering an existing Session ID).
A Session ID is a unique address people can use to contact you on Session. As Session explains, the reason using a Session ID is better than using a phone number or email address is, “Your Session ID is totally private, anonymous, and has no connection to your real identity.” Signal and other messaging apps that identify you with a phone number cannot give you this anonymity.
Once you create a Session ID, Session will ask you to pick your display name, and tell Session how to handle push notifications. And once that’s all done, Session will show you your Recovery Phrase and give you the opportunity to store it somewhere safe.
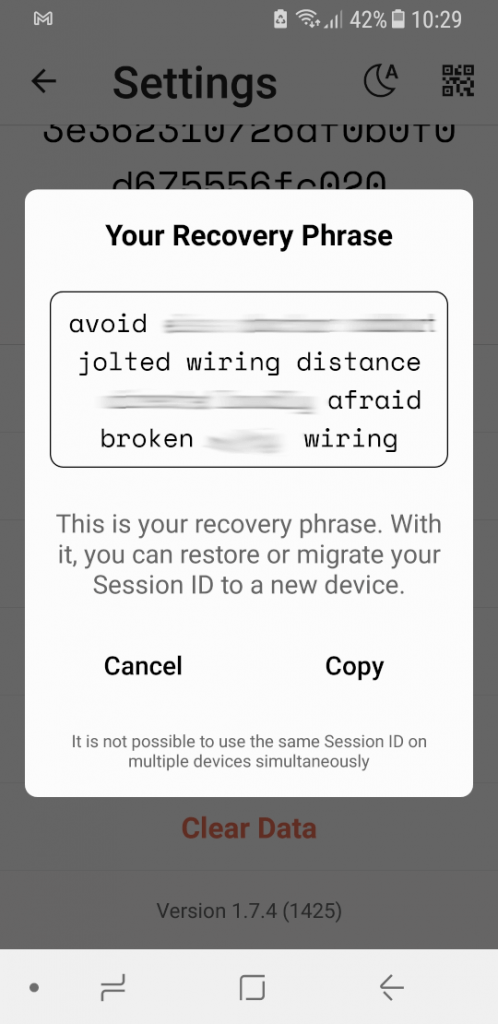
A Recovery Phrase is a string of words that you can enter to recover your account if you lose the Session ID, or change to a new device. To restore your Session ID, launch Session and tap Continue your Session. Session will give you the opportunity to enter your Recovery Phrase and get back to where you were when you last used that Session ID.
With all that out of the way, you are finally ready to start working with Session.
Working with Session
At first, Session will seem pretty dead. That’s because you still need to connect with people. While a service like Signal, you can scan your phone’s contact list looking for phone numbers that are registered as Signal users, Session needs you to tell it who to connect to. You do that by creating a New Session. A New Session is a chat session that you initiate by entering the Session ID of the person you want to chat with.
How do you know the Session ID of the person you want to chat with? You either get them to give it to you, or you scan a QR code that contains their Session ID. Unless you happen to be physically located in the same place, thereby able to pass the Session ID or display the QR code directly, one of you will need to share your Session ID with the other to get this thing started. You’ll need to use a different communication medium (another secure messenger app, perhaps) to make this happen.
Once you enter someone’s Session ID, you can send them a message. Once they accept it, you can freely exchange messages like any other chat app.
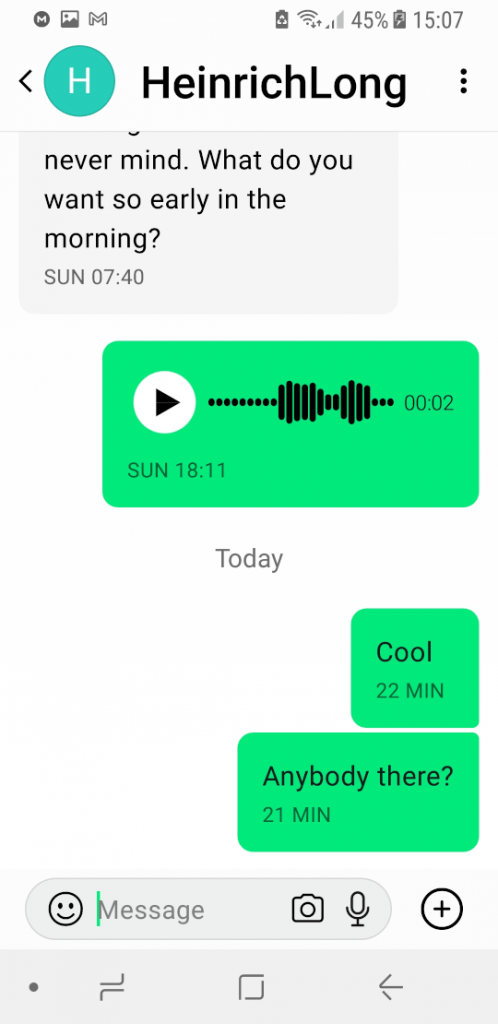
Tapping the icon for a contact opens your ongoing chat session with that contact.
Beyond basic chatting, Session has a number of additional useful features. Here are some of them:
- Encrypted groups – Create closed groups (up to 10 people previously; now up to 100) or huge open groups (no size limit).
- Voice messages – Create and share encrypted voice messages.
- Attachments – Message attachments are encrypted too.
- Safety Numbers – Verify that you are communicating with the device you expect to be talking to by comparing safety numbers.
Session Windows Desktop
Downloading and installing the Sessions Windows Desktop client follows the standard “install a Windows app” process.
Note: If you want to use the Session Linux Desktop, you’ll need to install it as an AppImage. If you don’t know how to work with this portable Linux file package, click this link for a short video tutorial.
Running and configuring Session Desktop
Once you’ve got the desktop downloaded and installed, you need to fire it up. You’ll want to connect your desktop client to your mobile device. You can do this by selecting Sign In, instead of Create Account, then selecting Link Device to Existing Session ID and following the instructions. The Session desktop apps I tested for this review were easy to use to get going and use.
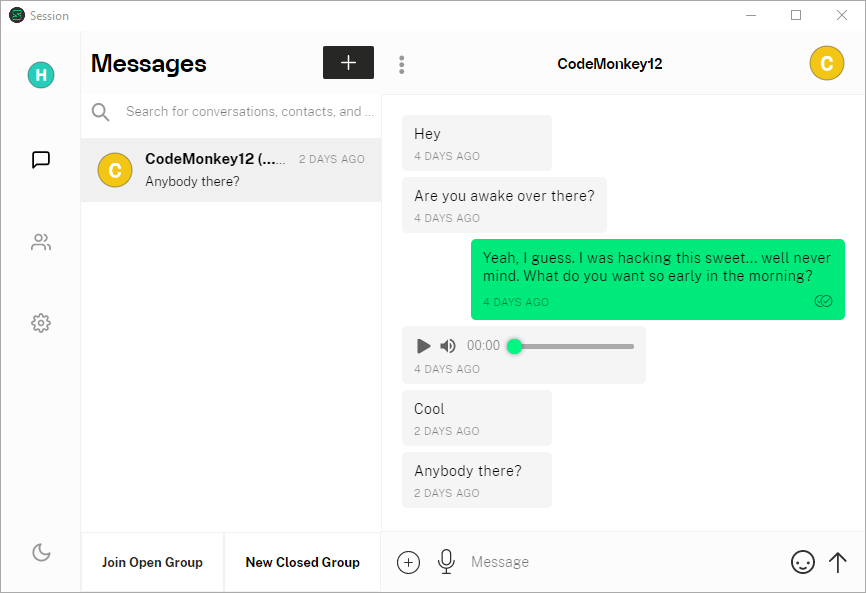
Note: Once you get the desktop app up and running, you will need to enter your contacts again. That’s because Session multidevice isn’t ready yet.
With the volume of changes coming out of the Session team, it can be hard to keep track of all the feature changes. If you intend to use this product, we suggest that you make time to check the Session blog to keep up with the ever-improving feature set of Session.
Comments